For any organization, IT security is essential. With rising incidents and threats, security has become a bigger part of the IT budget. Many organizations have had less than stellar results in defending against the hackers.
With lives on the line, IT security is mission critical for healthcare providers. There have been no successful intrusions or attacks on one particular healthcare provider thanks to outsourcing. “We estimated we were stopping around 2,000 to 3,000 attempts per month, ” says John Haltom, network director for Erlanger Healthcare Systems in Chattanooga, Tennessee. “Yet in the first month alone, SecureWorks, our outsourcing service provider, logged over 200,000 threats that were denied. We didn’t realize how vulnerable and lucky we were.”
The Growing Threat and Cost
The CERT Coordination Center, founded in 1988, was the first computer security incident response team. It is a non-academic unit of Carnegie Mellon University, funded primarily by the U.S. Department of Defense and a number of federal civil agencies to quickly and effectively coordinate communication among experts during security emergencies.
Almost half — 44.5 percent — of the incidents CERT recorded since 1988 occurred in a single year. The figure below from CERT demonstrates the increasing number of threats in greater detail.
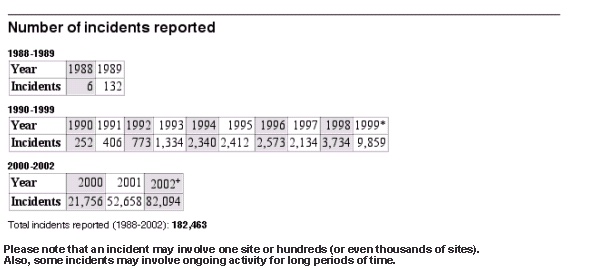
In September of that year, Information Security Magazine released a report on its survey of 215 IT practitioners. An average of 10.6 percent of the IT budget was for security.
The size of the enterprises was relatively evenly spaced. Some of the results reflected in the figures below are not only eye opening, but also frightening.
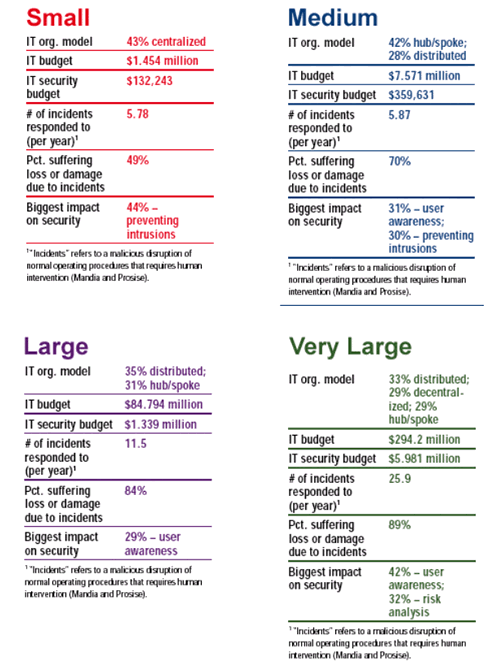
Eric Hemmendinger, research director for Aberdeen Group of Boston, Massachusetts, explains these statistics. “A lot of what looks like an attack is not targeted to the enterprise. The attacks are broad based and may be targeted at every firm that a provider hosts or provides connectivity for. Companies, for the most part, think of these attacks as something that pose risks. It is not combating, it is defending.” he says.
Attempting to meet the growing threat of intrusions has become a focal point for enterprises and has become major portion of IT budgets. Hemmendinger points out that the incidents are going up much faster than staffing. “Incidents are growing at 50 percent a year. Do you know of any organization increasing its IT staff 50 percent a year?” he asks. Hemmendinger says companies that don’t have some form of automation in place “will fail.”
Eliminating the Threat
Erlanger Health System is a regional health provider. Founded in 1891, Erlanger is affiliated with the University of Tennessee College of Medicine, which serves southeast Tennessee and north Georgia with four campuses. “Our problems were very simple. We could not implement virus/attack signature catching-methods in a timely manner,” says Haltom.
Erlanger evaluated several options and service providers. Erlanger outsourced to SecureWorks, of Atlanta, Georgia founded in 1999. Haltom says its “24x7x365 model and manned operations center were very pivotal to our deployment strategy.”
SecureWorks was founded with team members offering a wealth of IT security expertise including a background from CERT. SecureWorks offers a different approach to managed IT security operation: its system operates in front of the firewall and deflects intrusions or traps them until they can be identified.
Erlanger chose to use SecureWorks iSensor–essentially a box between the firewall and the router loaded with automated programmed functions to examine incoming and outgoing traffic. It monitors, filters and manages all traffic going in and out of the client next work. iSensor interfaces with the SecureWorks secure operations center in two-way communication.
Haltom says installation and deployment was “a breeze. The system took approximately one hour to get fully operational, a minor miracle. We had a few minor scanning setup arrangements that we worked out over the next couple of days, but nothing major.” Mike Cote, president and CEO of SecureWorks, nonchalantly adds, “It is basically three plugs.”
Cote says that little training is required for the Erlanger staff. “There is very little client training because they fully outsource their Internet security to us. The only real training is to teach them how to understand and read our reports.”
SecureWorks performs trend and threat analysis on an internal database with over three million alerts relating to potential or threatened attacks. SecureWorks also has networks and systems called honeypots, designed to attract hackers to watch what they do. Cote adds, “We also have a lab where we have guys play hacker with the operations guys and set up a war game.”
Winning the War In Cyber Space
Haltom estimates that to do it in house would require at least three additional staff members and that “still could not match the level of service we obtain from SecureWorks.”
Hemmendinger submits that, “Outsourcing to a specialized provider gives them more comprehensive protection than they could ever get on their own within a reasonable budget. The provider is accountable. If they fail they can be fired.”
Feeling secure about IT security is a relief for Haltom. “We have not had a single incident since we implemented this service. In the past we would have found out about the threat after the fact.”
Lessons from the Outsourcing Journal:
- Outsourcing can eliminate damage from hackers which is mission critical for healthcare providers who are required by law to keep their data secure.
- Most companies underestimate the threats to their IT security.
- Outsourcing IT security reduces the cost of staffing.

